Simplify Windows App Control, Achieve Essential Eight Compliance.
PoliEze is the control plane that makes Windows App Control simple, scalable, and secure—helping you reduce risk, ensure compliance, and maintain full control.
Accelerate Essential Eight Compliance
Fast-track Application Control—one of the toughest Essential Eight requirements—with built-in governance and reporting.Unified Monitoring &
Alerts
Prevent Unauthorised Policy Changes
Stop rogue policies from disabling your security stack and compromising compliance.Control Application with Confidence
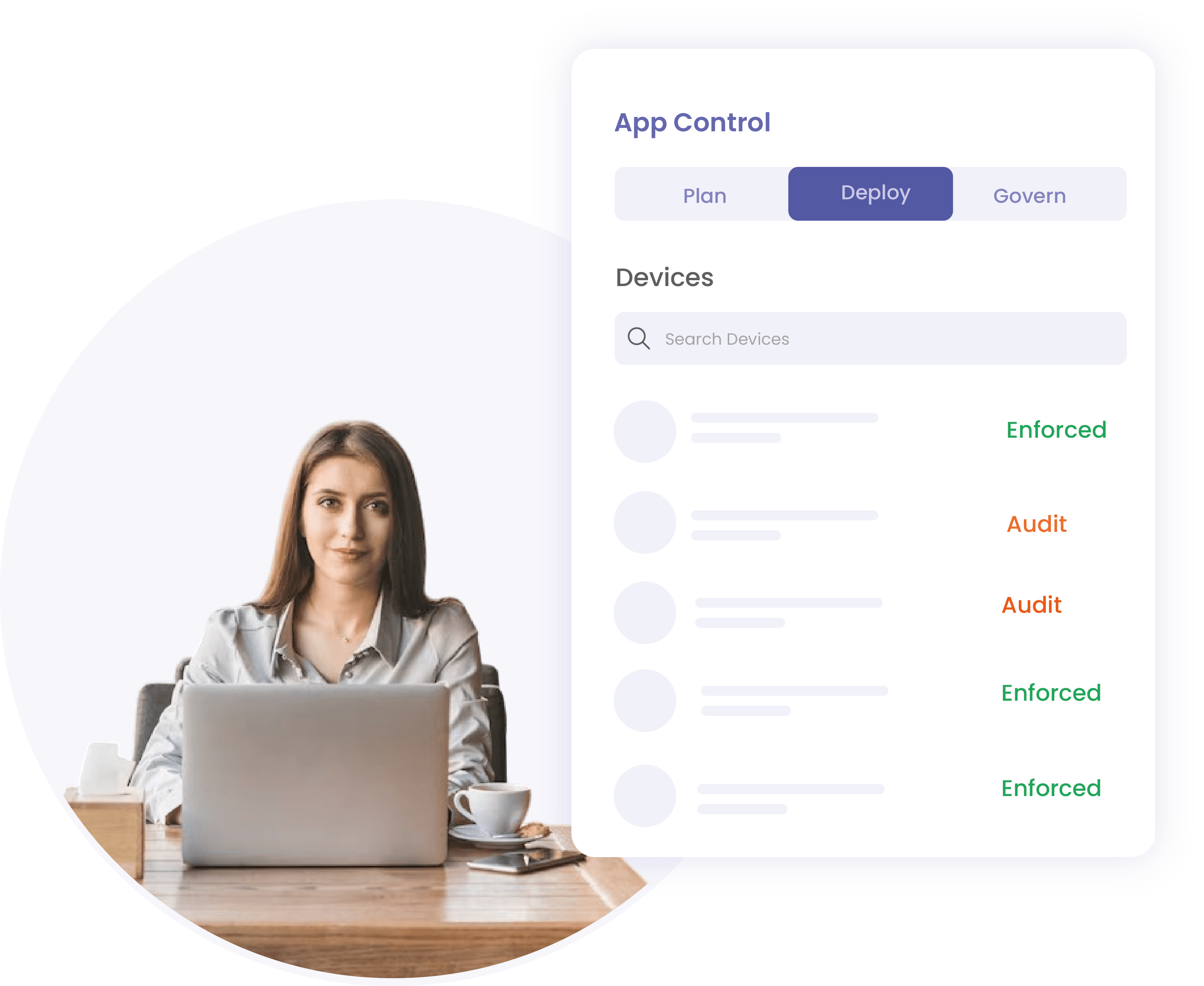
Implement Windows App Control policies seamlessly with guided workflows and safe policy transition options. Achieve compliance with the Australian Cyber Security Centre's (ACSC) Essential Eight by readily addressing a key control. -
Effortlessly Manage Windows App Control Policies
-
Seamless Administration
-
User-Friendly Interface
-
Workflow-Driven Approach
Effortlessly Manage Windows App Control Policies
Seamless Administration
User-Friendly Interface
Workflow-Driven Approach
Policy Lifecycle Management Process
Streamline the entire policy lifecycle, from initial setup through full operation, effortlessly.
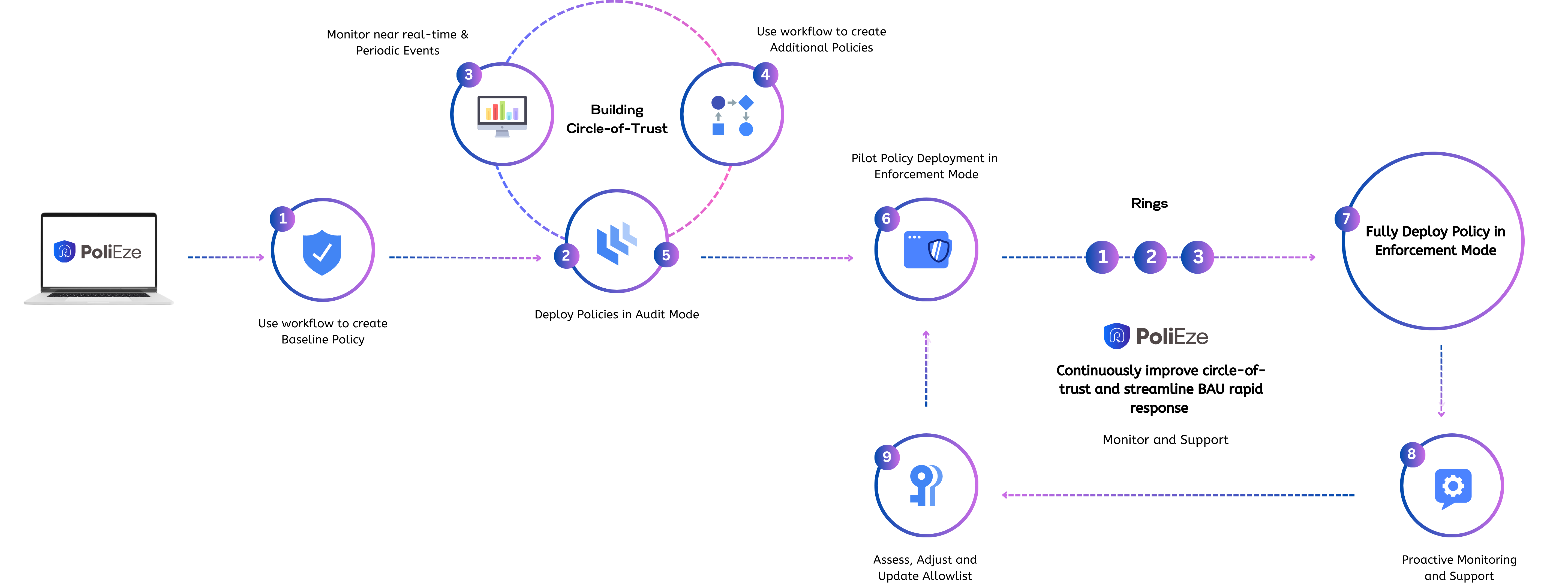
Easily implement and manage robust Windows App Control policies with our intuitive platform!
Explore the PoliEze PlatformAre you ready to elevate your organisation’s security to the next level?
Implementing Windows App Control policies is your gateway to a safer, more efficient digital environment. Safeguard your systems, streamline application management, and ensure compliance with ease.
Exclusive Opportunity for Early Adopters
Join the first three PoliEze customers and gain access to premium onboarding, extended usage benefits, and dedicated support—designed to accelerate your success.
-
Assisted Onboarding
-
6 Months Free Licensing
-
Premium white-glove Support
Key Features
Centralised Policy Management
Easily manage application control policies from a single, unified platform.Environment Auditing & Enforcement
Audit systems and enforce tailored policies that suit your operational needs.Secure Policy Reversal
Safely roll back policy changes with full traceability and access control.Simplified Governance
Streamline policy approvals and oversight with centralised governance tools.Operational Efficiency
Reduce manual effort and improve team productivity.ACSC Essential Eight Compliance
Support compliance with Australian cybersecurity standards through robust controls.Achieve ASD Essential Eight Compliance – Strengthen Your Application Control Pillar with PoliEze
We help organisations meet the Application Control requirements of the Australian Cyber Security Centre’s Essential Eight through a fast, efficient, and secure approach.
Book a Demo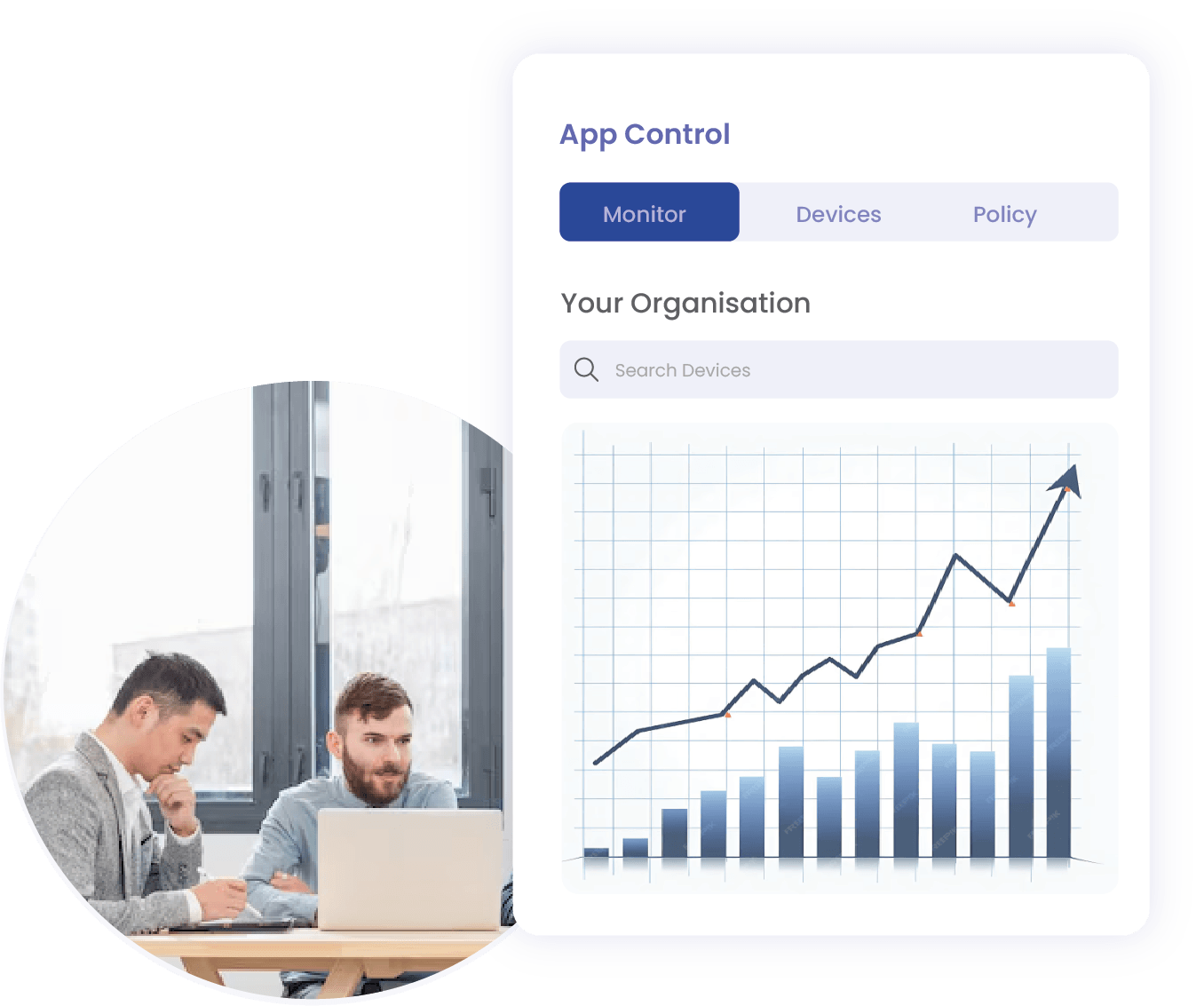
80% faster
Deploy application control policies in weeks, enabling quicker alignment with compliance goals.
Save Up to 60%
Reduce project and operational costs with streamlined workflows and automation.
80% Stronger Protection
Prevent malware, ransomware, and unauthorised software execution with robust policy enforcement.
90% Easier Oversight
Manage policies effortlessly with a workflow-driven interface that enhances visibility and control.
Your Control Plane for Application Control in the Windows Ecosystem
PoliEze empowers organisations to design, manage, and operationalize application control policies—supporting alignment with the ASD Essential Eight framework.
Centralised Policy Management
PoliEze provides a single interface to manage application control policies across your environment, offering full visibility, governance, and control.
UI-Driven Policy Creation
Design policies using intuitive wizards and guided workflows—no scripting or deep technical expertise required.
Compliance & Governance Support
Ensure consistency and auditability across your application control strategy, helping meet regulatory and cybersecurity standards like ASD Essential Eight.
Operational Efficiency
Streamline policy design and updates without impacting endpoint performance, enabling teams to move faster with reduced overhead.
Your Questions, Answered
Are you ready to elevate your organisation’s security to the next level?
Monitor real-time and periodic Windows App Control policy compliance reports. Track executable usage across your enterprise and standardise application version controls.
